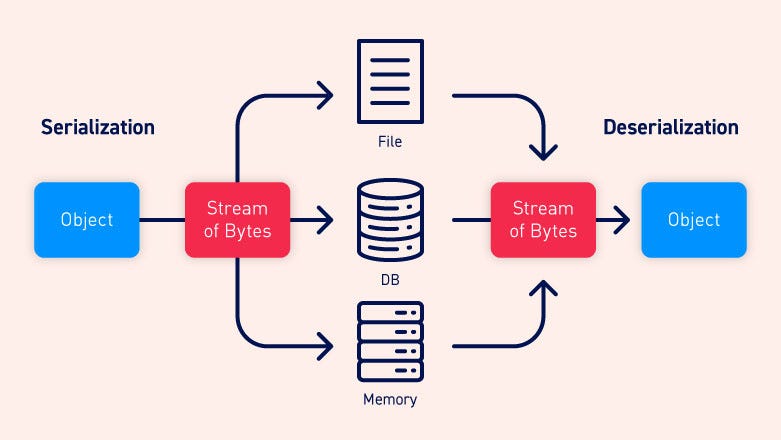
Serialization vs Deserialization
Serialization is the process of converting objects to a sequential stream of bytes so that it can be easily stored in a database or transmitted over a network. Deserialization is the exact opposite of serialization. It is the process of converting this sequential stream of bytes to a fully functional object.
The object’s state is also persisted which means that the object’s attributes are preserved, along with their assigned values. The process of preventing a field from being serialized varies from language to language.
What is insecure deserialization?
Insecure deserialization is when user-controllable data is deserialized by an application. This allows an attacker to manipulate serialized objects and pass malicious data into the application code. It is possible to replace the serialized object with an object of a completely different class.
It is virtually impossible to implement validation or sanitization to account for every eventuality. These checks are also fundamentally flawed as they rely on checking the data after it has been deserialized, which in many cases will be too late to prevent the attack as you will see in the exploitation examples later.
How to prevent insecure deserialization vulnerabilities
Deserialization of user input should be avoided unless necessary. If you do need to deserialize data from untrusted sources, incorporate robust measures to make sure that the data has not been tampered with. For example, you could implement a digital signature to check the integrity of the data. However, remember that any checks must take place before beginning the deserialization process. Otherwise, they are of little use.
Exploiting insecure deserialization in PHP
Basics of PHP Deserialization

Lines 2–15: Declaring a PHP class called Car which has 3 attributes model, manufacturer and colour. Each of them has different access specifiers for demonstration purposes. The parameterized constructor is used for initializing the attributes.
Line 16: Creating an object of class Car.
Lines 18,19: Serializing the object created in Line #16. Serialization creates some non-printable characters like \x00 so we are replacing it with \x00 so that we can view the output properly.
#cybersecurity #insecure-deserialization #application-security #security #programming